Advanced Cybersecurity APT Simulation & Threat Hunting
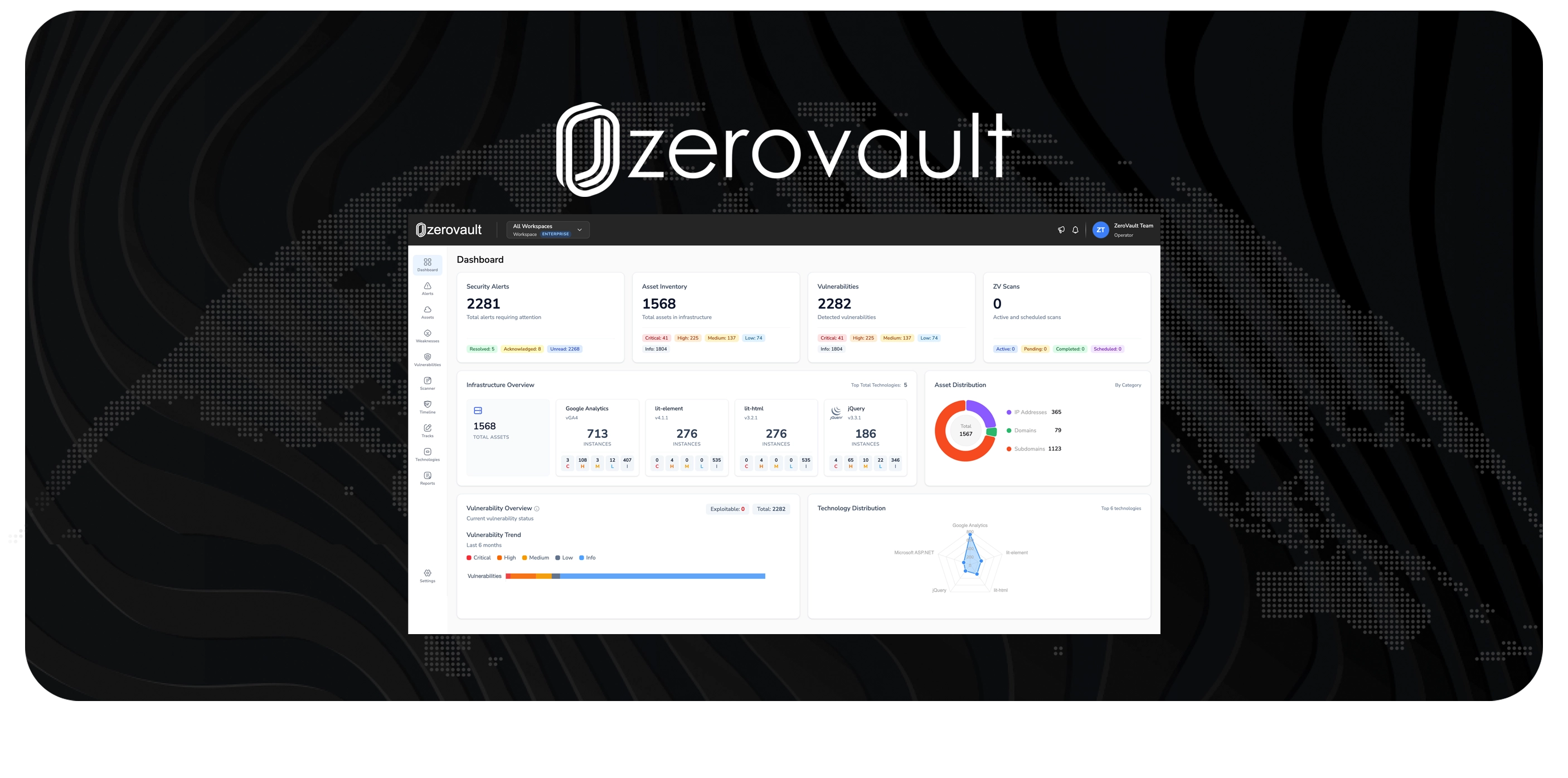
HawkTrace provides enterprise-grade cybersecurity solutions, threat hunting, and advanced security services to protect your organization's digital assets. Powered by ZeroVault exposure management platform and expert security consulting services.
APT Attack
Simulation
Advanced persistent threat detection.
HawkTrace conducts sophisticated attack simulations from nation-state adversary perspectives. Our APT simulation methodology validates your defenses against advanced persistent threats through multi-stage attack chains, custom malware development, and stealth operation techniques. Comprehensive threat intelligence reports provide actionable defensive strategies.
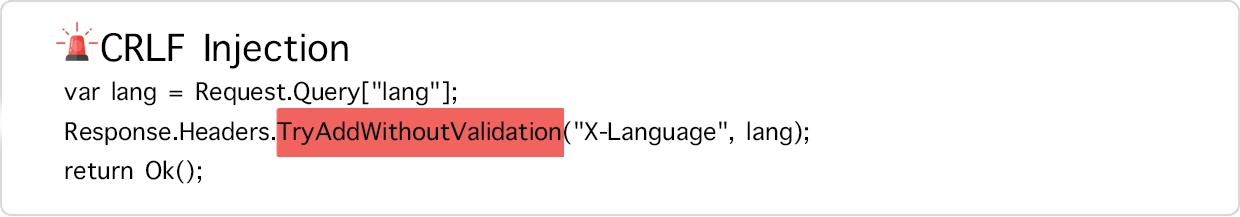
Source Code Analysis
Deep security code review.
Enterprise source code security analysis leveraging automated SAST scanning combined with expert manual review by certified security researchers. Identify SQL injection, cross-site scripting (XSS), authentication bypasses, and cryptographic weaknesses before production deployment. Ensure OWASP Top 10 compliance and validate secure coding practices across your development lifecycle.


Red Team Operations
Offensive security testing.
Comprehensive adversary simulation leveraging MITRE ATT&CK framework, custom exploit development, and advanced persistence techniques. HawkTrace Red Team operations test external perimeter security, internal network defenses, application security controls, and physical security measures. Validate incident response capabilities and identify complex attack chains before malicious actors exploit them.
Threat Hunting
Proactive threat detection.
Advanced threat hunting combining behavioral analytics, hypothesis-driven investigation, and threat intelligence correlation. Identify advanced persistent threats (APTs), insider threats, ransomware, and data exfiltration attempts that evade automated defenses. Continuous hunting operations with expert security analysts reduce dwell time and prevent security incidents.
By the Numbers
Trusted by enterprises worldwide for critical security operations
Trusted by Enterprise Organizations
Leading organizations across critical industries trust HawkTrace for their security operations and exposure management needs.
HawkTrace transformed our security posture. Their APT simulation revealed critical vulnerabilities we never knew existed, and their expert team helped us build robust defenses.